Leverage incident detection and monitoring – Implementing DevSecOps with AWS
- Blog
- Leverage incident detection and monitoring – Implementing DevSecOps with AWS
Amazon Macie is a threat detection service that uses machine learning and pattern-matching capabilities to identify sensitive data being stored in S3. Customers can also define custom patterns that are used by the service to identify risks and raise security findings in AWS Security Hub, a threat detection, aggregation, and remediation service. All your pipeline logs can be fed into such services for continuous automatic analysis.
Similarly, for artifacts such as container images produced by CI/CD pipelines, Amazon Inspector can be used. It integrates with Amazon ECR and creates a finding for software vulnerabilities as soon as new container images are pushed.
Next, we’ll investigate ways of enforcing security in the pipeline, which covers the steps to protect the code and dependencies in the application.
Security in the pipeline
After securing the pipeline itself, the next step is to secure the application code. It’s a daunting task to come up with a list of all security risks introduced by the code and the associated dependencies. Secondly, even if developers are made aware of the risks, it’s not practical for them to manually scan their code on every single commit. Therefore, in this section, we will focus on the Automation pillar of the AEA framework, as introduced at the beginning of this chapter. These automations are largely covered by different types of security scans that are embedded into different stages of the CI/ CD pipelines. Additionally, I will highlight some open source tools that are commonly leveraged for continuous security feedback.
As shown in Figure 9.1, the idea is to make these scans an inherent part of your code, build, test, and deploy phases. This ensures that we are not waiting for security clearance until the very end and the problems are much easier to fix if the feedback is shared in small iterations, as and when new code is added:
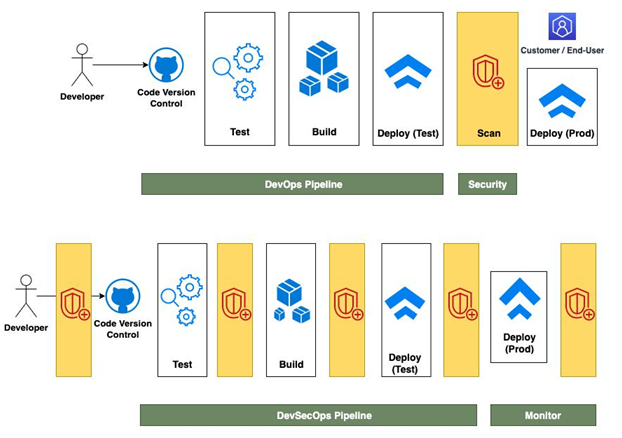
Figure 9.1 – Embedding security in all stages of CI/CD
In line with the shift left strategy we discussed previously, DevSecOps aims to enable developers to secure their code themselves. To facilitate this cultural transition, different types of code testing methods can be used to provide feedback to the developers.
© Copyright 2024 morningfun.org